Research
List of papers published by LASCA members
All
2024
Optimized One-Dimensional SQIsign Verification on Intel and Cortex-M4
IACR Transactions on Cryptographic Hardware and Embedded Systems
·
09 Dec 2024
·
doi:10.46586/tches.v2025.i1.497-522
Deep Learning Applied to Imbalanced Malware Datasets Classification
Journal of Internet Services and Applications
·
16 Sep 2024
·
doi:10.5753/jisa.2024.3907
Efficient isochronous fixed-weight sampling with applications to NTRU
IACR Communications in Cryptology
·
08 Jul 2024
·
doi:10.62056/a6n59qgxq
PQC-AMX: Accelerating Saber and FrodoKEM on the Apple M1 and M3 SoCs
2024 IEEE 31st Symposium on Computer Arithmetic (ARITH)
·
10 Jun 2024
·
doi:10.1109/arith61463.2024.00012
Verifiable FHE via Lattice-based SNARKs
IACR Communications in Cryptology
·
09 Apr 2024
·
doi:10.62056/a6ksdkp10
Towards Practical Transciphering for FHE with Setup Independent of the Plaintext Space
IACR Communications in Cryptology
·
09 Apr 2024
·
doi:10.62056/anxrxrxqi
Fast polynomial multiplication using matrix multiplication accelerators with applications to NTRU on Apple M1/M3 SoCs
IACR Communications in Cryptology
·
09 Apr 2024
·
doi:10.62056/a3txommol
NTRU-Based FHE for Larger Key and Message Space
Lecture Notes in Computer Science
·
01 Jan 2024
·
doi:10.1007/978-981-97-5025-2_8
Quasi-optimal Permutation Ranking and Applications to PERK
Lecture Notes in Computer Science
·
01 Jan 2024
·
doi:10.1007/978-3-031-64381-1_3
2023
Detecting Cryptography Misuses With Machine Learning: Graph Embeddings, Transfer Learning and Data Augmentation in Source Code Related Tasks
IEEE Transactions on Reliability
·
01 Dec 2023
·
doi:10.1109/TR.2023.3237849
Enhancing Malware Family Classification in the Microsoft Challenge Dataset via Transfer Learning
12th Latin-American Symposium on Dependable and Secure Computing
·
16 Oct 2023
·
doi:10.1145/3615366.3615374
A Minimal White-Box Dedicated Cipher Proposal Using Incompressible Lookup Tables: Space-Hard AES
Anais do XXIII Simpósio Brasileiro de Segurança da Informação e de Sistemas Computacionais (SBSeg 2023)
·
18 Sep 2023
·
doi:10.5753/sbseg.2023.233113
Improving FALCON’s Key Generation on ARMv8-A Platforms
Anais do XXIII Simpósio Brasileiro de Segurança da Informação e de Sistemas Computacionais (SBSeg 2023)
·
18 Sep 2023
·
doi:10.5753/sbseg.2023.233093
Real-Time Ego-Lane Detection in a Low-Cost Embedded Platform using CUDA-Based Implementation
Semina: Ciências Exatas e Tecnológicas
·
11 Sep 2023
·
doi:10.5433/1679-0375.2023.v44.48268
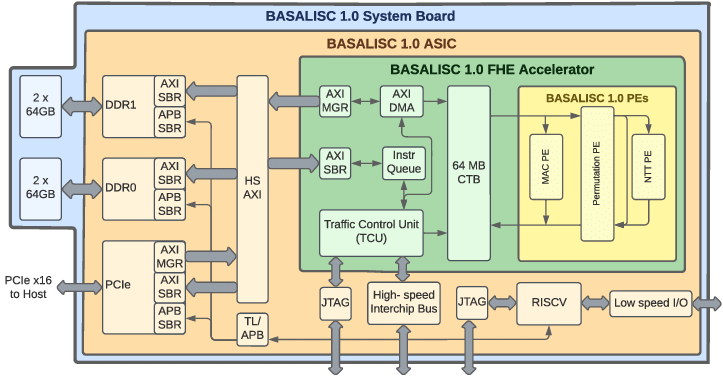
BASALISC: Programmable Hardware Accelerator for BGV Fully Homomorphic Encryption
IACR Transactions on Cryptographic Hardware and Embedded Systems
·
31 Aug 2023
·
doi:10.46586/tches.v2023.i4.32-57
Amortized Bootstrapping Revisited: Simpler, Asymptotically-Faster, Implemented
Lecture Notes in Computer Science
·
01 Jan 2023
·
doi:10.1007/978-981-99-8736-8_1
2022
Evaluation of modular multiplication techniques for Supersingular Isogeny Schemes on ARMv8 cores
Anais do XXII Simpósio Brasileiro de Segurança da Informação e de Sistemas Computacionais (SBSeg 2022)
·
12 Sep 2022
·
doi:10.5753/sbseg.2022.224951
Evaluation of CRYSTALS-Kyber and Saber on the ARMv8 architecture
Anais do XXII Simpósio Brasileiro de Segurança da Informação e de Sistemas Computacionais (SBSeg 2022)
·
12 Sep 2022
·
doi:10.5753/sbseg.2022.224450
AntiViruses under the microscope: A hands-on perspective
Computers & Security
·
01 Jan 2022
·
doi:10.1016/J.COSE.2021.102500
FINAL: Faster FHE Instantiated with NTRU and LWE
Lecture Notes in Computer Science
·
01 Jan 2022
·
doi:10.1007/978-3-031-22966-4_7
2021
The Ring-LWE Problem in Lattice-Based Cryptography: The Case of Twisted Embeddings
Entropy
·
26 Aug 2021
·
doi:10.3390/e23091108
One Size Does Not Fit All
ACM Transactions on Privacy and Security
·
21 Jan 2021
·
doi:10.1145/3429741
Tutte’s 3-flow Conjecture for almost even graphs
Procedia Computer Science
·
01 Jan 2021
·
doi:10.1016/J.PROCS.2021.11.035
Bootstrapping Fully Homomorphic Encryption over the Integers in Less than One Second
Lecture Notes in Computer Science
·
01 Jan 2021
·
doi:10.1007/978-3-030-75245-3_13
2020
Using Graph Embeddings and Machine Learning to Detect Cryptography Misuse in Source Code
2020 19th IEEE International Conference on Machine Learning and Applications (ICMLA)
·
01 Dec 2020
·
doi:10.1109/ICMLA51294.2020.00171
We need to talk about antiviruses: challenges & pitfalls of AV evaluations
Computers & Security
·
01 Aug 2020
·
doi:10.1016/j.cose.2020.101859
Fast AES Implementation Using ARMv8 ASIMD Without Cryptography Extension
Lecture Notes in Computer Science
·
01 Jan 2020
·
doi:10.1007/978-3-030-40921-0_5
Isogeny formulas for Jacobi intersection and twisted hessian curves
Advances in Mathematics of Communications
·
01 Jan 2020
·
doi:10.3934/AMC.2020048
Applied cryptography and network security. Part 1
Springer
·
01 Jan 2020
·
isbn:978-3-030-57808-4
2019
Analysis, comparison and assessment of the behavior of malware and goodware
Resumos do...
·
20 Dec 2019
·
doi:10.20396/revpibic2720192100
Characterizing lattices for cryptography
Resumos do...
·
20 Dec 2019
·
doi:10.20396/revpibic2720192087
Understanding How to Use Static Analysis Tools for Detecting Cryptography Misuse in Software
IEEE Transactions on Reliability
·
01 Dec 2019
·
doi:10.1109/tr.2019.2937214
Linux Malware Behavior Description
Resumos do...
·
30 Nov 2019
·
doi:10.20396/revpibic2720192426
Choosing parameters for trellis-based encryption systems
Resumos do...
·
30 Nov 2019
·
doi:10.20396/revpibic2720191576
A Secure White Box Implementation of AES Against First Order DCA
Anais do XIX Simpósio Brasileiro de Segurança da Informação e de Sistemas Computacionais (SBSeg 2019)
·
02 Sep 2019
·
doi:10.5753/sbseg.2019.13986
High-performance Implementation of Elliptic Curve Cryptography Using Vector Instructions
ACM Transactions on Mathematical Software
·
30 Jul 2019
·
doi:10.1145/3309759
The AV says: Your Hardware Definitions Were Updated!
2019 14th International Symposium on Reconfigurable Communication-centric Systems-on-Chip (ReCoSoC)
·
01 Jul 2019
·
doi:10.1109/RECOSOC48741.2019.9034972
“VANILLA” malware: vanishing antiviruses by interleaving layers and layers of attacks
Journal of Computer Virology and Hacking Techniques
·
11 Jun 2019
·
doi:10.1007/s11416-019-00333-y
On Fair Cost Facility Location Games with Non-singleton Players
Electronic Notes in Theoretical Computer Science
·
01 Apr 2019
·
doi:10.1016/j.entcs.2019.04.003
Fast White-Box Implementations of Dedicated Ciphers on the ARMv8 Architecture
Lecture Notes in Computer Science
·
01 Jan 2019
·
doi:10.1007/978-3-030-30530-7_17
2018
White Box Implementations of Dedicated Ciphers on the ARM NEON Architecture
Anais do XVIII Simpósio Brasileiro de Segurança da Informação e de Sistemas Computacionais (SBSeg 2018)
·
25 Oct 2018
·
doi:10.5753/sbseg.2018.4264
Leveraging ontologies and machine-learning techniques for malware analysis into Android permissions ecosystems
Computers & Security
·
01 Sep 2018
·
doi:10.1016/j.cose.2018.07.013
Who Watches the Watchmen
ACM Computing Surveys
·
13 Jul 2018
·
doi:10.1145/3199673
Connecting the dots: Toward accountable machine-learning printer attribution methods
Journal of Visual Communication and Image Representation
·
01 May 2018
·
doi:10.1016/j.jvcir.2018.04.002
Enhancing Branch Monitoring for Security Purposes
ACM Transactions on Privacy and Security
·
02 Jan 2018
·
doi:10.1145/3152162
Malicious Software Classification Using VGG16 Deep Neural Network’s Bottleneck Features
Advances in Intelligent Systems and Computing
·
01 Jan 2018
·
doi:10.1007/978-3-319-77028-4_9
Lumus: Dynamically Uncovering Evasive Android Applications
Lecture Notes in Computer Science
·
01 Jan 2018
·
doi:10.1007/978-3-319-99136-8_3
2017
Malicious Software Classification Using Transfer Learning of ResNet-50 Deep Neural Network
2017 16th IEEE International Conference on Machine Learning and Applications (ICMLA)
·
01 Dec 2017
·
doi:10.1109/ICMLA.2017.00-19
Practical Evaluation of Static Analysis Tools for Cryptography: Benchmarking Method and Case Study
2017 IEEE 28th International Symposium on Software Reliability Engineering (ISSRE)
·
01 Oct 2017
·
doi:10.1109/ISSRE.2017.27
Non-Cooperative Facility Location Games: a Survey
Revista de Informática Teórica e Aplicada
·
02 Aug 2017
·
doi:10.22456/2175-2745.71429
The other guys: automated analysis of marginalized malware
Journal of Computer Virology and Hacking Techniques
·
27 Feb 2017
·
doi:10.1007/s11416-017-0292-8
Non-interactive Privacy-preserving k-NN Classifier
Proceedings of the 3rd International Conference on Information Systems Security and Privacy
·
01 Jan 2017
·
doi:10.5220/0006187703620371
Non-cooperative capacitated facility location games
Information Processing Letters
·
01 Jan 2017
·
doi:10.1016/j.ipl.2016.09.001
2016
Detecção de técnicas de anti-forense em programas maliciosos
Anais do Congresso de Iniciação Científica da Unicamp
·
22 Oct 2016
·
doi:10.19146/pibic-2016-51820
Mining Cryptography Misuse in Online Forums
2016 IEEE International Conference on Software Quality, Reliability and Security Companion (QRS-C)
·
01 Aug 2016
·
doi:10.1109/QRS-C.2016.23
Towards a Methodology for the Development of Secure Cryptographic Software
2016 International Conference on Software Security and Assurance (ICSSA)
·
01 Aug 2016
·
doi:10.1109/ICSSA.2016.12
ACBuilder: A tool for hardware architecture security evaluation
2016 IEEE International Symposium on Hardware Oriented Security and Trust (HOST)
·
01 May 2016
·
doi:10.1109/HST.2016.7495564
An ontology of suspicious software behavior
Applied Ontology
·
22 Mar 2016
·
doi:10.3233/AO-160163
Going Native: Using a Large-Scale Analysis of Android Apps to Create a Practical Native-Code Sandboxing Policy
Proceedings 2016 Network and Distributed System Security Symposium
·
01 Jan 2016
·
doi:10.14722/NDSS.2016.23384
2015
MALICIOUS SOFTWARE IDENTIFICATION THROUGH OPERATING SYSTEM MONITORING
Anais do Congresso de Iniciação Científica da Unicamp
·
20 Nov 2015
·
doi:10.19146/pibic-2015-37604
Return on security investment for cloud computing
Proceedings of the 7th International Conference on Management of computational and collective intElligence in Digital EcoSystems
·
25 Oct 2015
·
doi:10.1145/2857218.2857254
Hardware Security Evaluation Using Assurance Case Models
2015 10th International Conference on Availability, Reliability and Security
·
01 Aug 2015
·
doi:10.1109/ARES.2015.60
Toward a Taxonomy of Malware Behaviors
The Computer Journal
·
13 Jul 2015
·
doi:10.1093/comjnl/bxv047
Security and system architecture: comparison of Android customizations
Proceedings of the 8th ACM Conference on Security & Privacy in Wireless and Mobile Networks
·
22 Jun 2015
·
doi:10.1145/2766498.2766519
Security Testing Methodology for Evaluation of Web Services Robustness - Case: XML Injection
2015 IEEE World Congress on Services
·
01 Jun 2015
·
doi:10.1109/SERVICES.2015.53
Efficient and Secure Elliptic Curve Cryptography for 8-bit AVR Microcontrollers
Lecture Notes in Computer Science
·
01 Jan 2015
·
doi:10.1007/978-3-319-24126-5_17
Assurance Cases as a Didactic Tool for Information Security
IFIP Advances in Information and Communication Technology
·
01 Jan 2015
·
doi:10.1007/978-3-319-18500-2_2
Adaptive Key Recovery Attacks on NTRU-Based Somewhat Homomorphic Encryption Schemes
Lecture Notes in Computer Science
·
01 Jan 2015
·
doi:10.1007/978-3-319-17470-9_17
2014
An approach to security-SLA in cloud computing environment
2014 IEEE Latin-America Conference on Communications (LATINCOM)
·
01 Nov 2014
·
doi:10.1109/LATINCOM.2014.7041843
Identifying Android malware using dynamically obtained features
Journal of Computer Virology and Hacking Techniques
·
17 Oct 2014
·
doi:10.1007/s11416-014-0226-7
Ontology for malware behavior: A core model proposal
2014 IEEE 23rd International WETICE Conference
·
01 Jun 2014
·
doi:10.1109/WETICE.2014.72
2013
FORTUNA—A framework for the design and development of hardware-based secure systems
Journal of Systems and Software
·
01 Aug 2013
·
doi:10.1016/j.jss.2013.03.059
E-commerce of digital items and the problem of item validation: introducing the concept of reversible degradation
Applicable Algebra in Engineering, Communication and Computing
·
02 Jul 2013
·
doi:10.1007/s00200-013-0197-9
Case Study: On the Security of Key Storage on PCs
2013 12th IEEE International Conference on Trust, Security and Privacy in Computing and Communications
·
01 Jul 2013
·
doi:10.1109/TrustCom.2013.203
An empirical analysis of malicious internet banking software behavior
Proceedings of the 28th Annual ACM Symposium on Applied Computing
·
18 Mar 2013
·
doi:10.1145/2480362.2480704
Fast Software Polynomial Multiplication on ARM Processors Using the NEON Engine
Lecture Notes in Computer Science
·
01 Jan 2013
·
doi:10.1007/978-3-642-40588-4_10
2012
A methodology for management of cloud computing using security criteria
2012 IEEE Latin America Conference on Cloud Computing and Communications (LatinCloud)
·
01 Nov 2012
·
doi:10.1109/LatinCloud.2012.6508157
A hybrid framework to analyze web and OS malware
2012 IEEE International Conference on Communications (ICC)
·
01 Jun 2012
·
doi:10.1109/ICC.2012.6364108
Pinpointing Malicious Activities through Network and System-Level Malware Execution Behavior
Lecture Notes in Computer Science
·
01 Jan 2012
·
doi:10.1007/978-3-642-31128-4_20
Interactive, Visual-Aided Tools to Analyze Malware Behavior
Lecture Notes in Computer Science
·
01 Jan 2012
·
doi:10.1007/978-3-642-31128-4_22
Interactive Analysis of Computer Scenarios through Parallel Coordinates Graphics
Lecture Notes in Computer Science
·
01 Jan 2012
·
doi:10.1007/978-3-642-31128-4_23
2011
LWE-based identification schemes
2011 IEEE Information Theory Workshop
·
01 Oct 2011
·
doi:10.1109/ITW.2011.6089439
FORTUNA - A probabilistic framework for early design stages of hardware-based secure systems
2011 5th International Conference on Network and System Security
·
01 Sep 2011
·
doi:10.1109/ICNSS.2011.6059999
TinyPBC: Pairings for authenticated identity-based non-interactive key distribution in sensor networks
Computer Communications
·
01 Mar 2011
·
doi:10.1016/j.comcom.2010.05.013
On the Smoothed Price of Anarchy of the Traffic Assignment Problem
Schloss Dagstuhl – Leibniz-Zentrum für Informatik
·
01 Jan 2011
·
doi:10.4230/OASIcs.ATMOS.2011.122
2010
T-DRE
Proceedings of the 26th Annual Computer Security Applications Conference
·
06 Dec 2010
·
doi:10.1145/1920261.1920291
Scalable model‐based configuration management of security services in complex enterprise networks
Software: Practice and Experience
·
19 Oct 2010
·
doi:10.1002/spe.1014
Kolline
Proceedings of the 28th ACM International Conference on Design of Communication
·
27 Sep 2010
·
doi:10.1145/1878450.1878465
Efficient implementation of elliptic curve cryptography in wireless sensors
Advances in Mathematics of Communications
·
01 May 2010
·
doi:10.3934/amc.2010.4.169
Formal validation of automated policy refinement in the management of network security systems
International Journal of Information Security
·
20 Feb 2010
·
doi:10.1007/s10207-010-0101-6
On Device Identity Establishment and Verification
Lecture Notes in Computer Science
·
01 Jan 2010
·
doi:10.1007/978-3-642-16441-5_9
2009
SB-RAWVec - A Semi-Blind Watermarking Method for Vector Maps
2009 IEEE International Conference on Communications
·
01 Jun 2009
·
doi:10.1109/ICC.2009.5199433
2008
TinyPBC: Pairings for authenticated identity-based non-interactive key distribution in sensor networks
2008 5th International Conference on Networked Sensing Systems
·
01 Jun 2008
·
doi:10.1109/INSS.2008.4610921
Model-based management of security services in complex network environments
NOMS 2008 - 2008 IEEE Network Operations and Management Symposium
·
01 Jan 2008
·
doi:10.1109/NOMS.2008.4575274
2007
SecLEACH—On the security of clustered sensor networks
Signal Processing
·
01 Dec 2007
·
doi:10.1016/j.sigpro.2007.05.016
TinyTate: Computing the Tate Pairing in Resource-Constrained Sensor Nodes
Sixth IEEE International Symposium on Network Computing and Applications (NCA 2007)
·
01 Jul 2007
·
doi:10.1109/NCA.2007.48
A Custom Instruction Approach for Hardware and Software Implementations of Finite Field Arithmetic over $$\mathbb{F}_{{2^{{163}} }} $$ using Gaussian Normal Bases
The Journal of VLSI Signal Processing Systems for Signal, Image, and Video Technology
·
27 Mar 2007
·
doi:10.1007/s11265-006-0015-8
SOS: Secure Overlay Sensornets
Fifth Annual IEEE International Conference on Pervasive Computing and Communications Workshops (PerComW'07)
·
01 Mar 2007
·
doi:10.1109/PERCOMW.2007.107
Identity-Based Encryption for Sensor Networks
Fifth Annual IEEE International Conference on Pervasive Computing and Communications Workshops (PerComW'07)
·
01 Mar 2007
·
doi:10.1109/PERCOMW.2007.56
A Policy-Based Framework for Interoperable Digital Content Management
2007 4th IEEE Consumer Communications and Networking Conference
·
01 Jan 2007
·
doi:10.1109/CCNC.2007.191
2006
Software multiplication using Gaussian normal bases
IEEE Transactions on Computers
·
01 Aug 2006
·
doi:10.1109/TC.2006.132
2005
Modellierung von Netzsicherheitsystemen umfangreicher vernetzter IT-Infrastrukturen
Lecture Notes in Informatics (LNI) Proceedings;P-68
·
01 Sep 2005
·
doi:10.17877/de290r-15888
Adenoids: a hybrid IDS based on the immune system
Proceedings of the 9th International Conference on Neural Information Processing, 2002. ICONIP '02.
·
[no date info]
·
doi:10.1109/ICONIP.2002.1202866
Policy Modeling and Refinement for Network Security Systems
Sixth IEEE International Workshop on Policies for Distributed Systems and Networks (POLICY'05)
·
[no date info]
·
doi:10.1109/POLICY.2005.24
An improvement of the Guajardo-Paar method for multiplication on non-supersingular elliptic curves
Proceedings SCCC'98. 18th International Conference of the Chilean Society of Computer Science (Cat. No.98EX212)
·
[no date info]
·
doi:10.1109/SCCC.1998.730787
A scheme for analyzing electronic payment systems
Proceedings 14th Annual Computer Security Applications Conference (Cat. No.98EX217)
·
[no date info]
·
doi:10.1109/CSAC.1998.738600
Web of Science
[no publisher info]
·
[no date info]
·
wosuid:WOS:000086437300016
Web of Science
[no publisher info]
·
[no date info]
·
wosuid:WOS:000088608600027
Two approaches for pay-per-use software construction
Proceedings Second International Workshop on Advanced Issues of E-Commerce and Web-Based Information Systems. WECWIS 2000
·
[no date info]
·
doi:10.1109/WECWIS.2000.853874
Web of Science
[no publisher info]
·
[no date info]
·
wosuid:WOS:000188940300033
Web of Science
[no publisher info]
·
[no date info]
·
wosuid:WOS:000224550900024
A custom instruction approach for hardware and software implementations of finite field arithmetic over F//sub 2/sup163// using Gaussian normal bases
Proceedings. 2005 IEEE International Conference on Field-Programmable Technology, 2005.
·
[no date info]
·
doi:10.1109/FPT.2005.1568517
SecLEACH - A Random Key Distribution Solution for Securing Clustered Sensor Networks
Fifth IEEE International Symposium on Network Computing and Applications (NCA'06)
·
[no date info]
·
doi:10.1109/NCA.2006.48
Web of Science
[no publisher info]
·
[no date info]
·
wosuid:WOS:000251784900006
Web of Science
[no publisher info]
·
[no date info]
·
wosuid:WOS:000247908000010
Implementing Cryptographic Pairings over Barreto-Naehrig Curves
Lecture Notes in Computer Science
·
[no date info]
·
doi:10.1007/978-3-540-73489-5_10
Web of Science
[no publisher info]
·
[no date info]
·
wosuid:WOS:000253413500019
NanoECC: Testing the Limits of Elliptic Curve Cryptography in Sensor Networks
Lecture Notes in Computer Science
·
[no date info]
·
doi:10.1007/978-3-540-77690-1_19
Web of Science
[no publisher info]
·
[no date info]
·
wosuid:WOS:000288935800009
Web of Science
[no publisher info]
·
[no date info]
·
wosuid:WOS:000342217900040
Web of Science
[no publisher info]
·
[no date info]
·
wosuid:PPRN:18908939
